How to get keys using nxpcrypto#
Introduction#
Nxpcrypto application is a collection of utilities for cryptographic operations provided by SPSDK. This jupyter notebook guide through process of generating keys using nxpcrypto. We recommend that you generate one set of keys for each project, which you store safely in a safe place, or protect it with a password.
Supported Commands#
cert - Group of command for working with x509 certificates.
generate - Generate certificate.
get-template - Generate the template of Certificate generation YML configuration file.
verify - Verify signature or public key in certificate.
digest - Computes digest/hash of the given file.
key - Group of commands for working with asymmetric keys.
convert - Convert Asymmetric key into various formats.
generate - NXP Key Generator Tool.
verify - Check whether provided keys form a key pair or represent the same key.
rot - Group of RoT commands.
calculate-hash - Calculate RoT hash.
export - Export RoT table.
signature - Group of commands for working with signature.
create - Sign the data with given private key.
verify - Verify the given signature with public key.
Types of keys by use#
Root of Trust Key (RoTK)/Super Root Key (SRK)
Image Signing Key (ISK)
Debug Credential Key (DCK)
Keys generation#
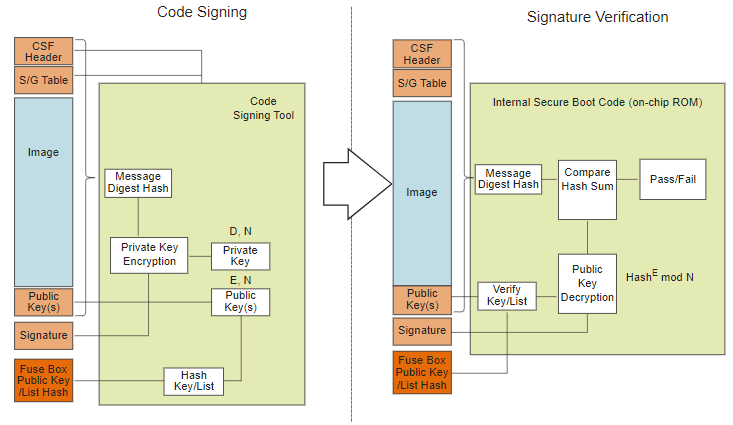
This section is used for key generation. Each time the keys generate command is called, a asymmetric key pair is generated. Key pair includes a public key (.pub) and a corresponding private key (.pem). Private keys are used to sign the images and public keys are used to validate the image during ISBC and ESBC phase (see below - scheme of secure boot process).
Possible RSA key types:
2048-bit (rsa2048)
3072-bit (rsa3072)
4096-bit (rsa4096)
Possible ECC key types:
secp256r1
secp384r1
secp521r1
Secure Boot Process#
%run ../init_notebook.ipynb
import os
WORKSPACE = "workspace/" # change this to path to your workspace
VERBOSITY = "-v" # verbosity of commands, might be -v or -vv for debug or blank for no additional info
# choose key type (rsa2048, rsa3072, rsa4096, secp256r1, secp384r1 or secp521r1)
KEY_TYPE = "secp384r1"
env: JUPYTER_SPSDK=1
Created `%!` as an alias for `%execute`.
# generate key pair for ROTK0/SRK0
ROTK0_PRIVATE_KEY_PATH = WORKSPACE + f"srk0_{KEY_TYPE}.pem"
ROTK0_PUBLIC_KEY_PATH = WORKSPACE + f"srk0_{KEY_TYPE}.pub"
%! nxpcrypto $VERBOSITY key generate -k $KEY_TYPE -o $ROTK0_PRIVATE_KEY_PATH --force
# verify that keys were generated
assert os.path.exists(ROTK0_PRIVATE_KEY_PATH)
assert os.path.exists(ROTK0_PUBLIC_KEY_PATH)
# generate key pair for ROTK1/SRK1
ROTK1_PRIVATE_KEY_PATH = WORKSPACE + f"srk1_{KEY_TYPE}.pem"
ROTK1_PUBLIC_KEY_PATH = WORKSPACE + f"srk1_{KEY_TYPE}.pub"
%! nxpcrypto $VERBOSITY key generate -k $KEY_TYPE -o $ROTK1_PRIVATE_KEY_PATH --force
# verify that keys were generated
assert os.path.exists(ROTK1_PRIVATE_KEY_PATH)
assert os.path.exists(ROTK1_PUBLIC_KEY_PATH)
# generate key pair for ROTK2/SRK2
ROTK2_PRIVATE_KEY_PATH = WORKSPACE + f"srk2_{KEY_TYPE}.pem"
ROTK2_PUBLIC_KEY_PATH = WORKSPACE + f"srk2_{KEY_TYPE}.pub"
%! nxpcrypto $VERBOSITY key generate -k $KEY_TYPE -o $ROTK2_PRIVATE_KEY_PATH --force
# verify that keys were generated
assert os.path.exists(ROTK2_PRIVATE_KEY_PATH)
assert os.path.exists(ROTK2_PUBLIC_KEY_PATH)
# generate key pair for ROTK3/SRK3
ROTK3_PRIVATE_KEY_PATH = WORKSPACE + f"srk3_{KEY_TYPE}.pem"
ROTK3_PUBLIC_KEY_PATH = WORKSPACE + f"srk3_{KEY_TYPE}.pub"
%! nxpcrypto $VERBOSITY key generate -k $KEY_TYPE -o $ROTK3_PRIVATE_KEY_PATH --force
# verify that keys were generated
assert os.path.exists(ROTK3_PRIVATE_KEY_PATH)
assert os.path.exists(ROTK3_PUBLIC_KEY_PATH)
# generate key pair for ISK
ISK_PRIVATE_KEY_PATH = WORKSPACE + f"imgkey_{KEY_TYPE}.pem"
ISK_PUBLIC_KEY_PATH = WORKSPACE + f"imgkey_{KEY_TYPE}.pub"
%! nxpcrypto $VERBOSITY key generate -k $KEY_TYPE -o $ISK_PRIVATE_KEY_PATH --force
# verify that keys were generated
assert os.path.exists(ISK_PRIVATE_KEY_PATH)
assert os.path.exists(ISK_PUBLIC_KEY_PATH)
# generate key pair for DCK
DCK_PRIVATE_KEY_PATH = WORKSPACE + f"dck_{KEY_TYPE}.pem"
DCK_PUBLIC_KEY_PATH = WORKSPACE + f"dck_{KEY_TYPE}.pub"
%! nxpcrypto $VERBOSITY key generate -k $KEY_TYPE -o $DCK_PRIVATE_KEY_PATH --force
# verify that keys were generated
assert os.path.exists(DCK_PRIVATE_KEY_PATH)
assert os.path.exists(DCK_PUBLIC_KEY_PATH)
nxpcrypto -v key generate -k secp384r1 -o workspace/srk0_secp384r1.pem --force
The key pair has been created: workspace\srk0_secp384r1.pub, workspace\srk0_secp384r1.pem
nxpcrypto -v key generate -k secp384r1 -o workspace/srk1_secp384r1.pem --force
The key pair has been created: workspace\srk1_secp384r1.pub, workspace\srk1_secp384r1.pem
nxpcrypto -v key generate -k secp384r1 -o workspace/srk2_secp384r1.pem --force
The key pair has been created: workspace\srk2_secp384r1.pub, workspace\srk2_secp384r1.pem
nxpcrypto -v key generate -k secp384r1 -o workspace/srk3_secp384r1.pem --force
The key pair has been created: workspace\srk3_secp384r1.pub, workspace\srk3_secp384r1.pem
nxpcrypto -v key generate -k secp384r1 -o workspace/imgkey_secp384r1.pem --force
The key pair has been created: workspace\imgkey_secp384r1.pub, workspace\imgkey_secp384r1.pem
nxpcrypto -v key generate -k secp384r1 -o workspace/dck_secp384r1.pem --force
The key pair has been created: workspace\dck_secp384r1.pub, workspace\dck_secp384r1.pem